In modern finance, trust is increasingly rooted in mathematics rather than institutions. As we build systems where identity, value and compliance processes must operate securely without compromising privacy, one cryptographic tool has proven itself indispensable: commitment schemes. These elegant mathematical constructions allow someone to “lock in” a message today, reveal it later, and give all parties involved the assurance that nothing has changed in between.
At the core of such schemes lies a simple but powerful idea. A commitment works much like a sealed envelope: you write a message, add some randomness like a handful of confetti to disguise it, then close the envelope with a wax seal before handing it over to someone else. In this scenario the confetti represents a dose of pure mathematical randomness that shields the message so that if someone were to examine the sealed envelope under a bright lamp, they would not be able to decipher what’s inside. Anyone can hold it, store it, or even pass it along, yet still remain in the dark about your message. Later you open the envelope by revealing both the message and the confetti (a.k.a. the randomness). With both pieces in hand, anyone can verify the correctness of the commitment, meaning the message is genuine and unchanged.
Two security properties are essential here. A commitment must be hiding, meaning no one can guess the message from the commitment alone. It must also be binding, which you can imagine as putting the sealed envelope into a locked box. The key that opens the box is uniquely tied to the message you put inside. For example, you can’t claim tomorrow that you wrote “yes” when yesterday’s message was “no”. The binding structure of the commitment locks your choice in place the moment it was created to allow perfect secrecy up front, and accountability later.
This conceptual foundation is what set the stage for the Pedersen Commitment (PC) scheme, which was introduced decades ago, but is still one of the most influential building blocks for privacy-preserving systems.
From Secret Sharing to Verifiability
The story of PC begins not with blockchains, but with an earlier breakthrough, namely Shamir’s secret sharing scheme. This scheme introduced a method for splitting a secret into n pieces such that any k of them could reconstruct the secret while fewer than k revealed nothing at all. Although beautifully secure, Shamir’s scheme lacked a mechanism for recipients to check whether the shares they received were correct. This verification problem led to the development of verifiable secret sharing, where commitments ensure that each participant can independently confirm the validity of their share.
To make this possible, a commitment scheme must interact smoothly with the algebra underlying the secret sharing. This is one of the benefits of Pedersen Commitments. Their structure is not just simple and secure – it’s mathematically compatible with the operations required for secret sharing and many types of zero-knowledge proofs as used in the Concordium blockchain.
The Mechanics Behind Pedersen Commitments
While Pedersen Commitments are often implemented using elliptic curves – as on the Concordium blockchain – the basic idea can be explained much more simply. PC starts with a setup that uses a few special numbers, and can be thought of as rules of a game. The only thing that matters is that no one knows a particular secret link between two of these numbers.
To make a commitment, you take your message and camouflage it with randomness, like the confetti mentioned above. The result is a commitment you can share publicly as it perfectly hides your data. The commitment also prevents you from changing the data later as long as you don’t know the secret link between the special numbers. This makes them simple, reliable building blocks for privacy-focused systems, including finance and payment systems.
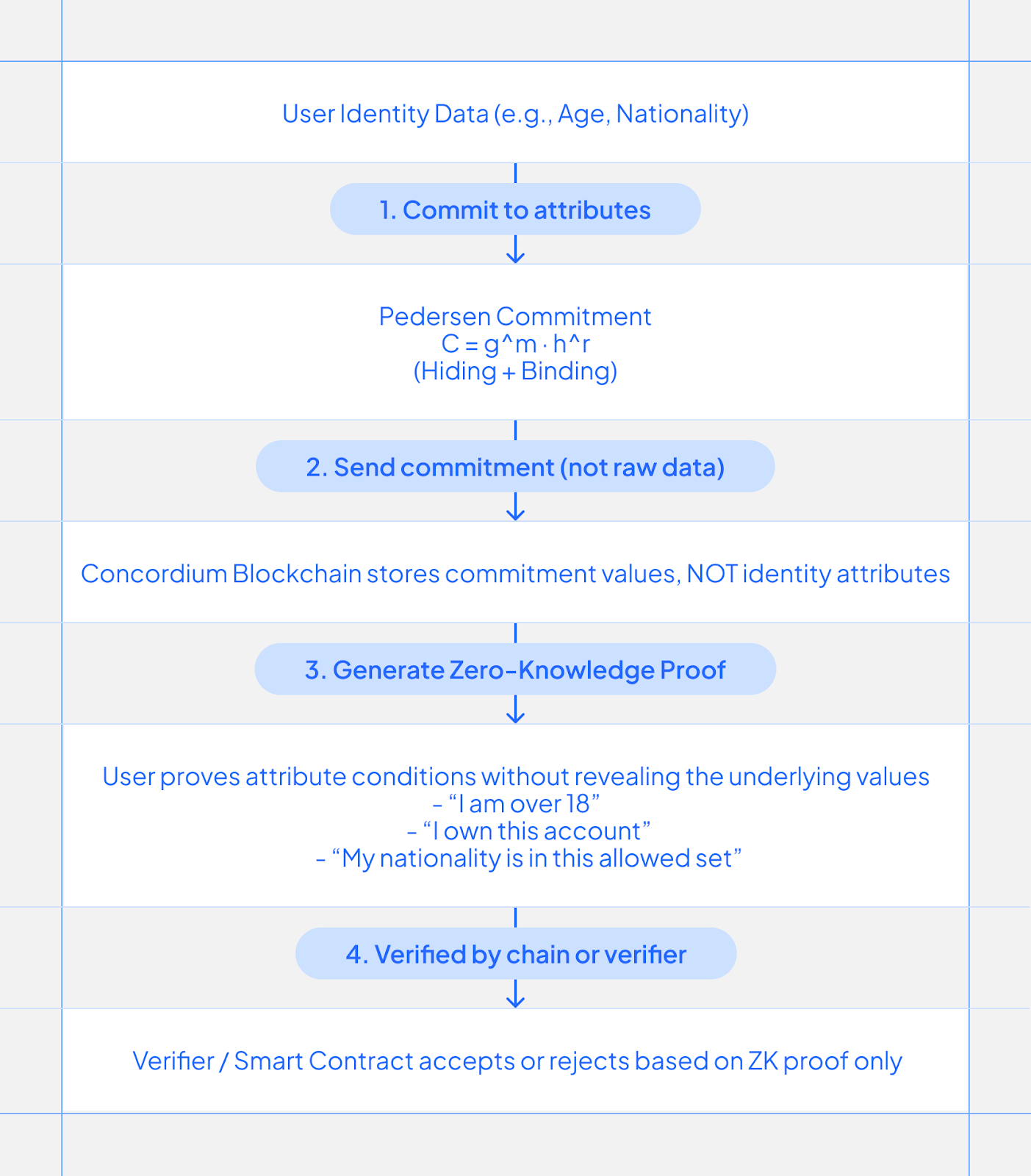
Further, PCs have another handy feature: if you combine two commitments, it’s like adding the original messages together behind the scenes. This makes it possible to build efficient privacy tools, like proving you’re over 18 without revealing your birthday.
Show Nothing, Prove Everything
The Concordium blockchain was designed with the central goal to link regulated, real-world identity with on-chain accounts without exposing personal information publicly. PCs enable exactly this. Attributes such as name, nationality, or date of birth are committed to, ensuring that:
- the blockchain reveals no personal data
- efficient zero-knowledge proofs can be made about the user
- users retain control over how and when their information is disclosed
In this scheme, a trader, for example, can prove they meet the qualifications to trade a regulated asset without revealing their full financial profile, or demonstrate they are compliant with EU market rules without exposing their identity or location. Concordium uses Sigma protocols and Bulletproofs for this. These are compact non-interactive zero-knowledge proof systems that leverage the properties of PCs.
The Quantum Horizon
Even the most robust systems will face future challenges with the rise of quantum computing. A sufficiently powerful quantum computer could break many of the computational assumptions underpinning classical cryptography, including the binding property of PCs. If this were to occur, an attacker could open a commitment in multiple ways, fabricating false attributes and undermining proof systems.
This is why researchers at Concordium are preparing to migrate to post-quantum secure commitment schemes. The reassuring news is that PCs remain unconditionally hiding. Even with a quantum computer, adversaries cannot extract personal data from historical commitments. This protects users from “harvesting attacks”, where encrypted or committed data is being collected in hopes of decrypting it later.
Mathematically Building Trust for a Resilient Financial Future
Pedersen Commitments have quietly powered some of the most advanced privacy technologies of the past three decades. As payments, trading, and digital identity converge on decentralized rails, their value–and the value of their successors–will only increase.
For financial systems to survive the coming technological shifts, preparing now is no luxury. It’s essential for maintaining trust in systems meant to last decades. More than ever, banks, payment providers and regulated trading platforms need assurances that the identities behind transactions remain private, that compliance checks remain verifiable, and that the confidentiality of historical data cannot be cracked open decades later.
As we continue developing Concordium, this pledge to future-proof, mathematically sound security remains at the heart of our design philosophy and the vision to shape the financial infrastructure for decades to come.
Learn more about the details in the Concordium Cryptographic Bluepaper.
About the Author
Dr. Torben Pryds Pedersen is a pioneering cryptographer best known for introducing the Pedersen Commitment scheme, one of the most widely used building blocks of modern privacy-preserving finance. His seminal 1991 paper on verifiable secret sharing has been cited over 4,000 times, shaping decades of research in cryptography, secure multiparty computation, and blockchain privacy. With a long career spanning both theoretical breakthroughs and applied innovation, he continues to help bridge advanced cryptography with real-world financial and compliance systems. His work remains central to projects like Concordium, where strong cryptographic guarantees and privacy-by-design are core to the platform’s mission.